Cybersecurity | Cloud Security
Evolved Techniques Explained and Lessons Learned From Recent Dropbox & Uber Hack
Image by the author
Cloud Computing gives phishers a new playground to harvest and grow their business. But not only that, but the impacts are much broader and more dangerous. No organization, small or big, is invulnerable to phishing attacks. Therefore, it’s critical to learn how you might be targeted and what you can do to prevent it.
SaaS-based phishing is already familiar. For example, over 90% of all data breaches are due to phishing, from stolen credentials to malicious URLs. Also, according to a report from Palo Alto Networks Unit 42, researchers have seen a massive increase in this abuse, with the data collected by the firm showing an enormous expansion of 1,100% from June 2021 to June 2022.
With more advancements in technology, not only can defenders leverage more sophisticated tools and techniques to detect and block phishing emails, links, and messages, but attackers are also improving on their side of the cat-and-mouse game.
While most social engineering attacks are delivered by email, one-third of IT professionals reported increased social engineering delivered via other communication platforms in 2022.
These include attacks delivered via:
- Video conferencing platforms (44%),
- Workforce messaging platforms (40%),
- Cloud-based file-sharing platforms (40%), and
- SMS (36%).
Moreover, phishing on social media is increasingly common, and in Q1 2022, LinkedIn users were targeted in 52% of all phishing attacks globally. According to Proofpoint’s 2022 State of the Phish report, employees at 74% of organizations have been sent fraudulent text messages (smishing), and the same percentage have been targeted on social media.
A Hard-to-Detect New Phishing Technique — SaaS-to-SaaS
All these could happen without the attacker touching the victim’s on-prem computers/ network. Since it all happened SaaS-to-SaaS, all the existing security measures, such as Anti-Spam gateway, sandboxing, and URL filtering, will not inspect. Thus, no alert will be generated.
Furthermore, with the rise of cloud office productivity and multi-user collaboration technologies, it is now possible for an attacker to host and share malicious documents, files, and even malware on the cloud infrastructure of these reputable domains while remaining undetected.
Since the Check Point Research findings in 2020, we saw the trend of using this “multi-stages” SaaS-to-SaaS phishing attack.
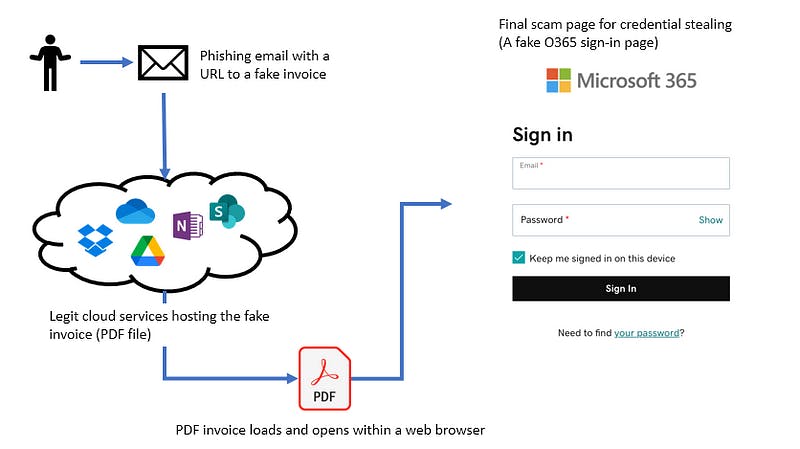
Example of Saa-to-SaaS phishing attack flow | Image by the author
The first stage of a phishing attack is frequently a fake invoice or secure document PDF hosted on cloud services. This document can be downloaded; however, it is essential to note that to facilitate use, these cloud services open the PDF for viewing, allowing it to load in the web browser without restriction or warning.
It is hard to detect because it didn’t necessarily hit the protection deployed. As we saw on the news, as AWS Cloud Phishing attempts in August, if phishing detection is implemented in the entrance and exit of emails, it will never see it happening.
All actions occurred in the Cloud (or multiple clouds); when the detection/ scanning took place, all things seemed legit and encrypted. Most likely, the phishing email will hit the victims’ machine, and all the magic will happen in the browser.
Multi-stage Cloud Phishing
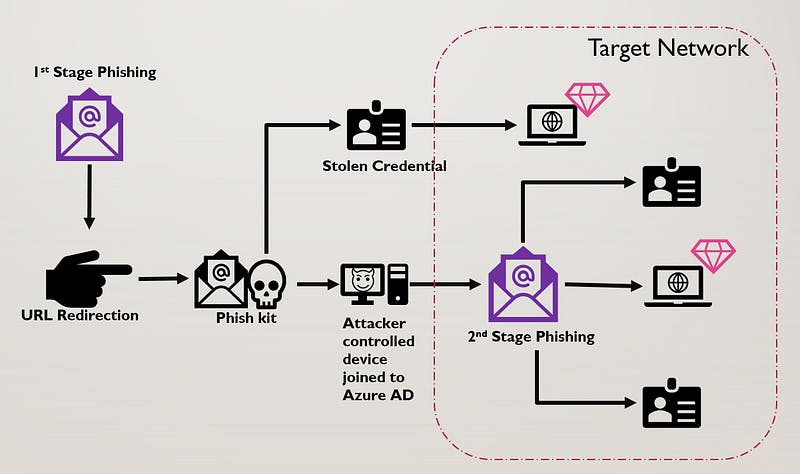
Multi-stage Cloud Phishing | Image by the author
Early this year, Microsoft warned of new phishing leveraging Azure ADs that prey upon those who don’t use multifactor authentication.
This attack is thriving now but not before because attackers take advantage of the concept of BYOD (Bring-Your-Own-Device) via the capability of device registration using newly stolen credentials, and cloud authentication is accessible anytime, anywhere.
Nothing out of the ordinary, it is a novel attack technique that combines traditional phishing with second-phase or even third-phase actions. The first stage steals an employee’s email like regular phishing attacks.
Yet, instead of attacking the victim, the second stage establishes a new Office 365 account on a rogue device in the victim’s name. Once established on the new computer, the victim’s user account (and or this case, its Azure Ad) is used to send internal phishing attacks (disguised as the victim) within the company or to customers using the legitimate email account.
If they want to gain more control or find a better “host,” they can find it via the first victim and then steal the second account by internal phishing. These multi-stage attacks appear legitimate and can even deploy malware on the company’s OneDrive or SharePoint systems.
ChatGPT (or Other AI)
According to HP Wolf Security research, phishing accounts for nearly 90% of malware attacks. But ChatGPT could make the whole situation even worse. Such intelligent 🧠 AI Chatbot can be a way to gather information through a human-like friendly chat. So the victim may not even know they are interacting with an AI.
Check Point Research recently published an interesting article demonstrating how AI models could create a full infection flow, from spear-phishing to reverse shell. Multiple scripts can be generated quickly, with variations. Complex attack processes can also be automated, using the LLMs APIs to generate other malicious artifacts.
Another risk is more prominent. AI technology like ChatGPT will enable attackers to blend the volume of massive phishing with a targeted attack (or spear-phishing). For example, say generic phishing attacks send out millions of spam in the form of emails, SMS (in the case of smashing), and social media posts. But these are easy to spot, resulting in low yield.
With the addition of an AI Chatbot, millions of spear phishing messages could be generated in seconds. Thus, the attackers can have the best of both worlds. Therefore in 2023, we will probably see some large-scale phishing that sends millions of unique messages generated within minutes. It would be a tremendous challenge for security teams.
Other Novel Phishing Techniques
QRishing
Attackers are now trying to deliver malware links via QR codes embedded in emails, which makes them difficult to detect for most email security solutions.
QRishing combines the words: “QR Codes” + “Phishing.” This indicates the attack is in the form of a QR code. It can potentially direct victims into connecting to an unsecured WiFi network while someone can easily capture what you are typing.
Some adversaries even stick malicious QR codes in restaurants or other public locations. Since the pandemic limits physical contact, QR codes are a popular tool for threat actors. We use it to access menus, check in for vaccines, and get public information. In addition, social engineering tactic is inserting fake QR codes into a phishing text (SMishing + QRishing) or social media platform. Upon scanning the malicious code, users are redirected to phishing sites, where the victim may be prompted to log in and steal their credentials.
SMishing
SMishing combines the words “phishing” and “SMS.” That means it is one kind of phishing sent across your mobile network in the form of text messages. Although the name uses SMS, this attack can happen on other messenger platforms, such as Facebook Messenger or WhatsApp.
Common Smishing attempts to focus on everyday necessities. Missed deliveries, late payments, bank notifications, fines, and urgent notices are examples of smishing attacks.
With so many people staying at home and so many daily online purchases, we’re awash in cardboard. It’s very challenging to keep track of everything coming into the house. Combining well-known delivery services with fake “delivery fee” notifications is the best recipe for a successful Smishing.
Crown Jewel = Developer Accounts
Why are threat actors trying to compromise developer accounts? And what can go wrong if they are stolen? Depending on the developer’s position, attackers gain access to nearly everything:
- SSH keys,
- API keys,
- Source Code,
- Production infrastructure,
- Access to CI/CD pipelines and,
- i.e., the works.
Assuming a compromise with the “best scenario,” a junior engineer’s account might be stolen. At the very least, this engineer has “commit” access to the source code. On the other hand, suppose the organization does not follow the best practices of software engineering, such as code reviews and restricting who can commit to the main branch. In that case, the attacker can modify the organization’s source code to alter and infect the final product.
In the worst-case scenario, which is also the most likely, the attacker will gain access to a senior developer with more permissions. This account could manually bypass some code checks, which will also have access to valuable resources (source code, SSH keys, secrets, credentials, API keys, CI/CD pipelines, and more). This scenario, where this kind of account is compromised, would be devastating for an organization. Developer accounts usually come with GitHub or other code repository access.
Dropbox & Uber
In September, Uber disclosed that hackers had stolen the personal information of about 57 million customers and drivers. Later, we discovered that the hack was related to a hard-coded credential obtained by a “remote social engineering attack.”
In November, Dropbox had a security incident due to a phishing attack against its developers. They were lured into filling in their Github credentials by a phishing email into a fake website, despite multifactor authentication (MFA) in place.
What makes these incidents scary is that this wasn’t just a random user from a business function; it was developers with privileged access to many Dropbox and Uber data.
MFA Fatigue
Both cases from these two giant tech companies implemented multifactor authentication. Still, hackers find a way to bypass or work around this measure that can prevent most credential theft.
In the case of Uber, the hacker (allegedly a 17-year-old) was creative and came up with a low-tech but very effective method — an “MFA-fatigue attack.” The attacker attempts to log in repeatedly, sending a flood of push requests to users asking the victim to confirm a sign-in. Once the victim stopped clicking “no” on their phone, followed by an “authorized login,” thus, MFA failed.
For the Dropbox case, which is much simpler. The phishing email purported to originate from the code integration and delivery platform, CircleCI. Then the realistic-looking phishing site tricked the developer into typing the credential and the one-time password. Thus, MFA also failed.
Code Repo and More
As we saw in these incidents, GitHub and other platforms in the continuous integration/ continuous deployment (CI/ CD) pipeline space are the new “crown jewels” for many companies. With the proper permissions, attackers can obtain intellectual property, source codes, and other sensitive data.
But it doesn’t stop there, as GitHub often integrates with other platforms, which lets the allowed “users” go even further. In addition, developers’ accounts are usually granted access to the deepest level, as maintaining and developing the core application may be part of their job responsibility. That makes the developer account a crown jewel for attackers.
How to Improve Your Phishing Defenses
According to industry statistics, the average organization receives dozens of phishing emails per day, with financial losses compounding as losses from malware and ransomware attacks drive up the average cost of landed phishing attacks year over year.
Facing all the threats highlighted requires extra effort, and while you can’t eliminate the risk of phishing attacks, you can learn from observed trends and incidents to better manage them. For example, here are the recommendations from the recent Zscaler report:
- Understand the risks to inform policy and technology decisions better
- Leverage automated tools and actionable intel to reduce phishing incidents
- Implement zero-trust architectures to limit the blast radius of successful attacks
- Deliver timely training to build security awareness and promote user reporting
- Simulate phishing attacks to identify gaps in your program
Apart from the five basic mitigations of phishing attacks, we can do more. Therefore, I will end this article with tips you can bring along. Knowing that phishers will eventually find a way to get to you, having a greater extent of cyber-resilience would be an excellent way to begin.
Tips #1: Multi-layered phishing defenses approach
Typical email security against phishing often relies exclusively on a single guard point, such as email gateways and endpoint/ mobile agents. Everything passing through that gate would depend on users being able to spot phishing messages. Not to mention attackers are now sharpening their weapons with multi-stage phishing.
Conversely, a layered defense approach could improve cyber-resilience without disrupting business productivity. Moreover, there would be multiple chances to detect and catch a phishing email. Even though some attacks get through, this approach will help with incident response and minimize the impact.
- Reach — Prevent the email from reaching the user’s inbox. This can be achieved by introducing anti-phishing security software such as spam filters. In addition, anti-spoofing controls should be implemented, such as; DMARC, DKIM, and SPF records.
- Identify — Most data breaches are initiated through a phishing email due to human error. Therefore, staff should have regular training in identifying the latest potential phishing emails. This will enable them to follow the company process when an incident does occur, which should include reporting the incident to the relevant team.
- Protect — Protections should be in place for when incidents do occur. These protections include but are not limited to; enforcing multifactor authentication (MFA), password managers, regular IT health checks, and endpoint defenses.
- Response — Staff should be able to report phishing incidents to the relevant team. A dedicated security logging and the alarming system should be in place, as well as an Incident Response Plan.
Tips #2: Just-in-time (JIT) Access Approach
Privilege access entails a significant danger, claims Gartner. The risk posed by users with standing privileges persists even with PAM tools, and it is considerable. They suggest just-in-time (JIT) solutions be used by identity and access management (IAM) leaders to finally achieve a posture of no standing privileges.
Gartner also provided a solution to counter it — The Just-in-Time approach. For example, when developers use these credentials to set up or modify production resources, granting them the appropriate permissions is crucial, with only the capabilities required to complete specified tasks.
The JIT approach, which deals with information security, only gives users access to privileged resources while working. This reduces the attack surface and eliminates the risk brought on by persistently held-over privileges.
Tips #3: Review Mailbox Forwarding
Threat actors use compromised accounts not only to steal internal data but also, for example:
- Read users’ emails,
- Distribute malware,
- Spamming,
- Learn about the user and to further launch second-stage phishing, and
- Forwarding emails to external recipients.
Attackers may set up email rules to conceal their malicious activities from the user to hide incoming emails in the compromised user mailbox. They may also create rules in the compromised user mailbox to delete emails, move them to a less visible folder, such as an RSS folder, or forward emails to an external account.
Emails can be manually or automatically forwarded using forwarding rules. Automatic forwarding can be accomplished in various ways, including Inbox Rules, Exchange Transport Rules (ETR), and SMTP Forwarding. While manual forwarding requires users to take direct action, they may need to be aware of all auto-forwarded emails.
It would be wise to schedule a review of all email forwarding rules to external addresses and check that it is not an unusual IP address and corresponds to the user’s usual activities.
Final Words
The reality is that no one can stop phishing entirely as long as the human factor is in the formula. As a result, the best we can do for the long term is to adopt Zero Trust Architecture for email security. It would be a much more granular design of the multi-layered defense approach.
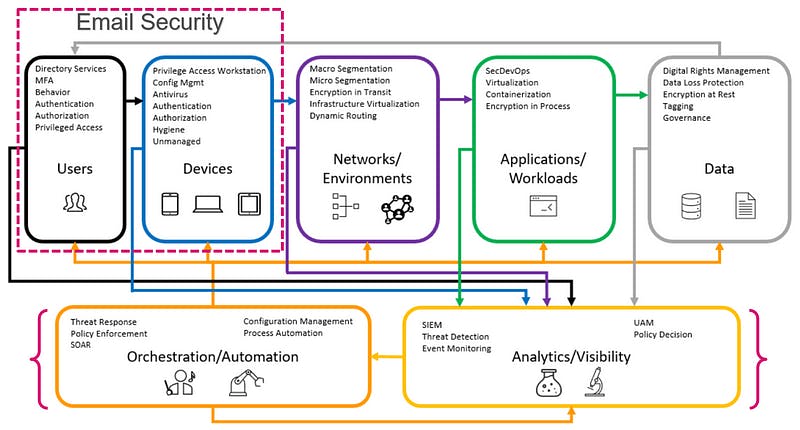
A Zero Trust approach to email | Image by the author
A Zero Trust approach to email can assist organizations in defending against email impersonation attacks by focusing on Authentication (Verifying User/ Device Trust) — ensuring that emails entering the corporate environment or landing in end users’ inboxes are from legitimate individuals, brands, and domains.
A privileged position exists for software developers in every technical organization. They are the lynchpin in any modern company because of their upstream access to the products distributed to clients and their access to production systems and infrastructure. The security organization would fail if developers weren’t protected, leading to catastrophe.
If you, unfortunately, fall for a phishing attack, please do the followings:
- Contact the IT department and let them know the situation
- Reset password for related applications
- Please don’t use a repeated password. Instead, reset the account with the same password as the applications above.
- Monitor the account with care for 30 days
Finally, NIST developed a method to help the security team to see why users click on the phishing email:
[The Phish Scale: NIST-Developed Method Helps IT Staff See Why Users Click on Fraudulent Emails](nist.gov/news-events/news/2020/09/phish-sca.. "nist.gov/news-events/news/2020/09/phish-sca..")
Thank you for reading. May InfoSec be with you🖖.
